Socket for Gitlab Pipeline
Socket fights vulnerabilities and provides visibility, defense-in-depth, and proactive supply chain protection for your open source dependencies. It is easy to integrate Socket into your Gitlab Pipeline to provide an extra layer of security against Supply Chain Attacks.
Adding Socket to your pipeline
Create your Socket Environment variables
-
Create a Socket API Key (Directions)
-
Log into Gitlab
-
Navigate to your project
-
Go to Settings -> CI/CD
-
Expand Variables
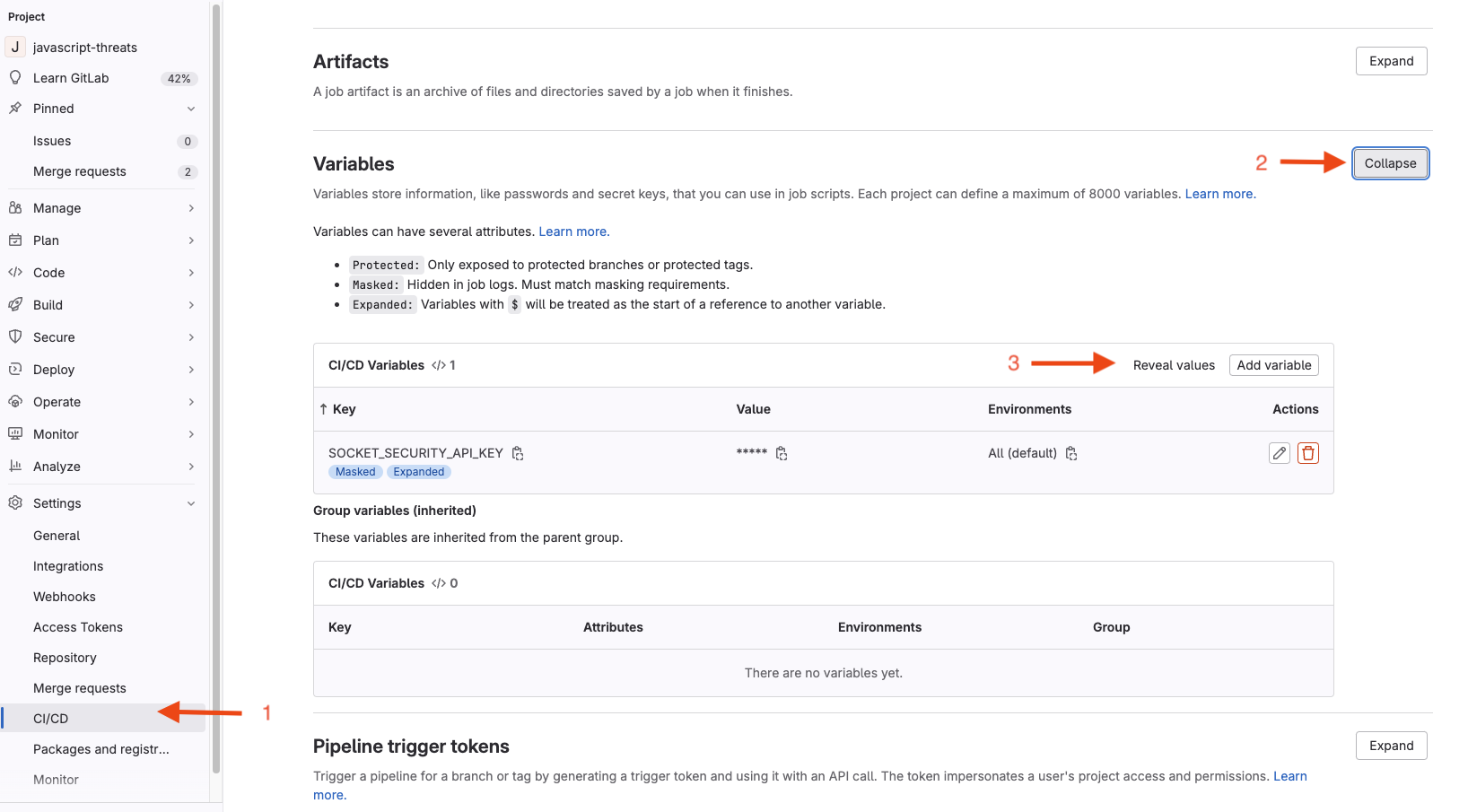
-
Do Add Variable
- Tick the "Masked and hidden" radio button for "Visibility" option
- Check the "Expand variable reference" box for the "Flags" option so that the variable can be expanded in the pipeline job execution. Note: "$" literals in variable values need to be escaped in GitLab.
- For the "Key:" field, enter the name "SOCKET_SECURITY_API_KEY"
- For the "Value:" field, enter your <Socket API Token>
-
Next, to add another variable called "GITLAB_TOKEN" for your Gitlab Token that has access to the Project
- First, let’s go generate the gitlab project access token value
- Go to Setting -> Access tokens
- Click on “Add new token” button
- Give a “Token name”
- Optional, given a token description
- For the role select the scoping as required per permission needs:
- Personal Access Token
- Role Reporter with scope api
- Group Access Tokens
- Role Reporter with scope api
- The Token needs to be granted access to the project or group
- Personal Access Token
- Then click on “Create project access token” button
- You will need to make a copy of the generated project access token for the next step.
- Go back to the CI/CD -> Variables (Expand it) -> Click on “Add variable”
-
Tick the “Masked” radio button for “Visibility” option
-
Check the "Expand variable reference" box for the "Flags" option
Protect variable:
- ✅ Enable if your jobs run only on protected branches/tags (recommended for secrets). Note that "Allow merge request pipelines to access protected variables and runners" should be enabled.
- ❌ Disable (uncheck) if your jobs must run on unprotected branches and need this token (Important!) Environment scope: All (or narrow if needed)
Why this matters
-
Protected = safer: Protected variables are only available in pipelines on protected branches/tags.
-
Unprotected usage: If a job needs the token on unprotected branches, you must uncheck Protect variable, or provide a separate, least-privilege token as an unprotected variable.
Tip: Prefer keeping sensitive tokens protected. Use $CI_JOB_TOKEN or a restricted-scope token for unprotected branches; reserve powerful tokens for protected branches only.
-
For the "Key:" field, enter the name "GITLAB_TOKEN"
-
For the "Value:" field, paste the generated <project_access_token> here
-
-
Sample screenshot
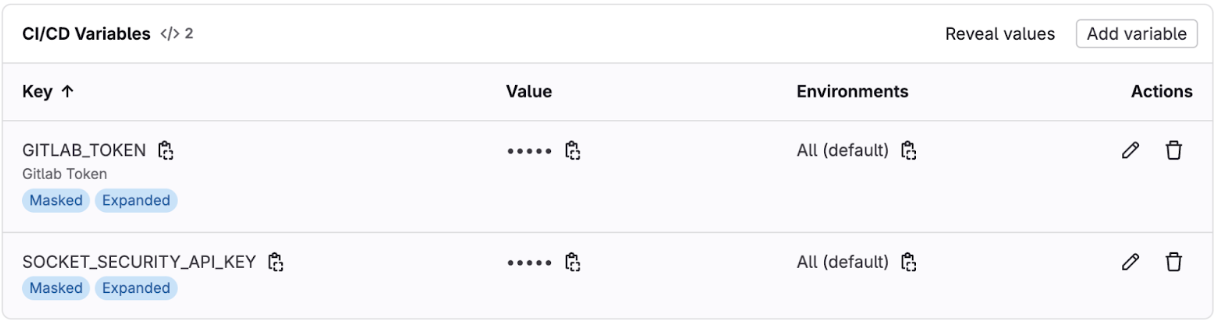
Example Gitlab Pipeline Setup
-
Go to Build
-
Go to Pipeline Editor
-
Paste the following Pipeline Yaml, or integrate with your existing code
# Socket Security GitLab CI Pipeline # This pipeline runs Socket Security scans on every commit to any branch # The CLI automatically detects most information from the git repository stages: - security-scan socket-security: stage: security-scan image: name: socketdev/cli:latest entrypoint: [""] # Override the entrypoint to run commands directly # Run on all branches and merge requests rules: - if: $CI_PIPELINE_SOURCE == "push" # Uncomment rule below to only run Socket CLI on changes to manifest files. # Note: You may miss new alerts for existing packages # changes: # - <manifest file> - if: $CI_PIPELINE_SOURCE == "merge_request_event" # Uncomment rule below to only run Socket CLI on changes to manifest files. # Note: You may miss new alerts for existing packages # changes: # - <manifest file> # Required for GitLab integration to work properly variables: SOCKET_SECURITY_API_KEY: $SOCKET_SECURITY_API_KEY GITLAB_TOKEN: $GITLAB_TOKEN # This is an option to help speed up the processing PIP_CACHE_DIR: "$CI_PROJECT_DIR/.cache/pip" # This variable is optional, configuration for the runner cache: paths: - .cache/pip/ script: # Run Socket CLI with minimal required parameters # The CLI automatically detects: # - Repository name from git # - Branch name from git # - Commit SHA from git (or CI_COMMIT_SHA) # - Commit message from git # - Committer information from git # - Default branch status from GitLab CI environment variables # - Changed files from git commit # - Merge request number from CI_MERGE_REQUEST_IID - | socketcli \ --target-path $CI_PROJECT_DIR \ --scm gitlab \ --pr-number ${CI_MERGE_REQUEST_IID:-0} -
Commit changes to your main branch or the current branch you are working on
Testing pipeline
-
Create a new branch
-
Modify or add a
package.json -
Create a new Merge request
-
Confirm that the Socket CI pipeline job ran
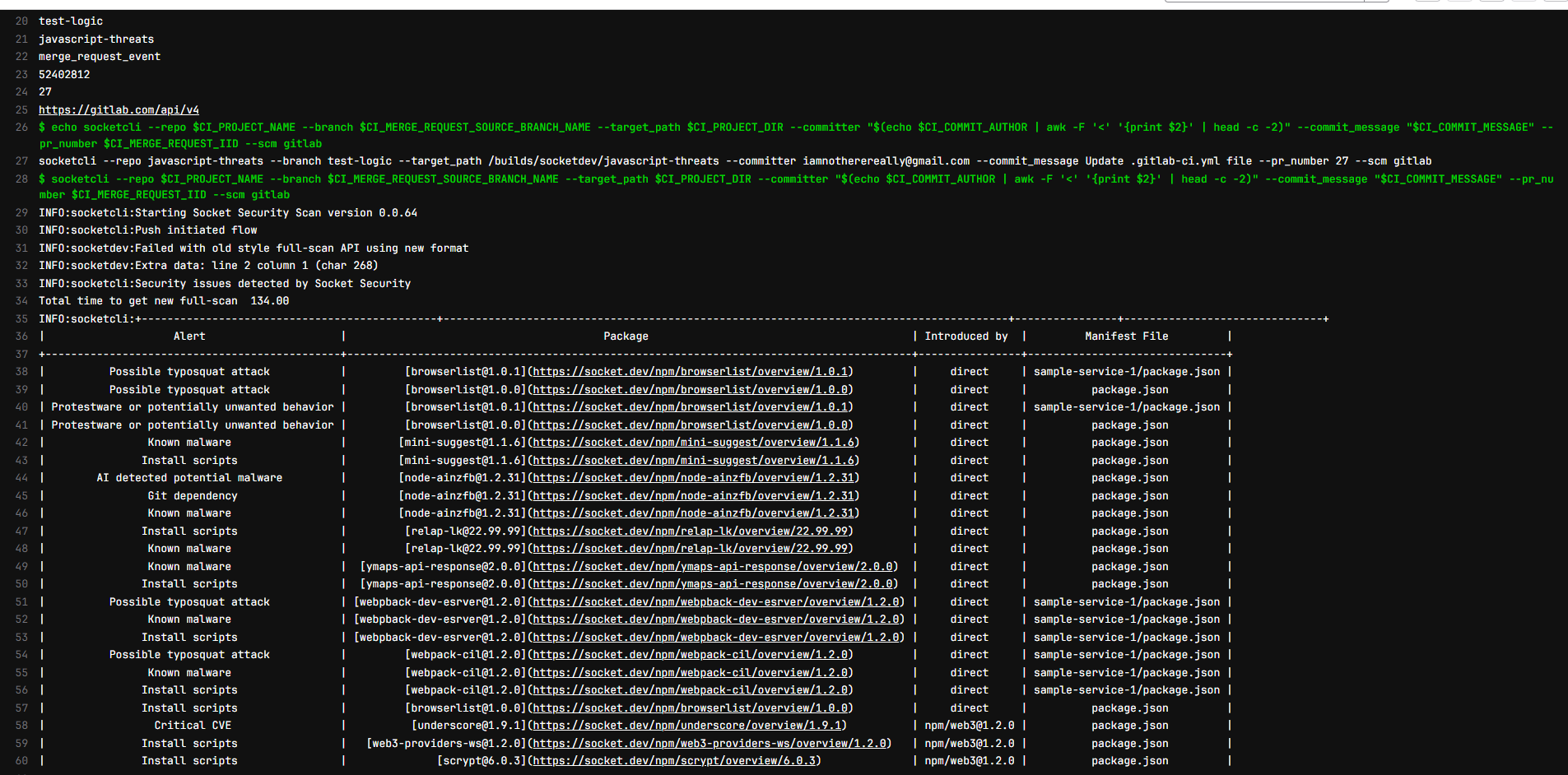
-
Confirm that for an unhealthy report a comment is left on the Merge request
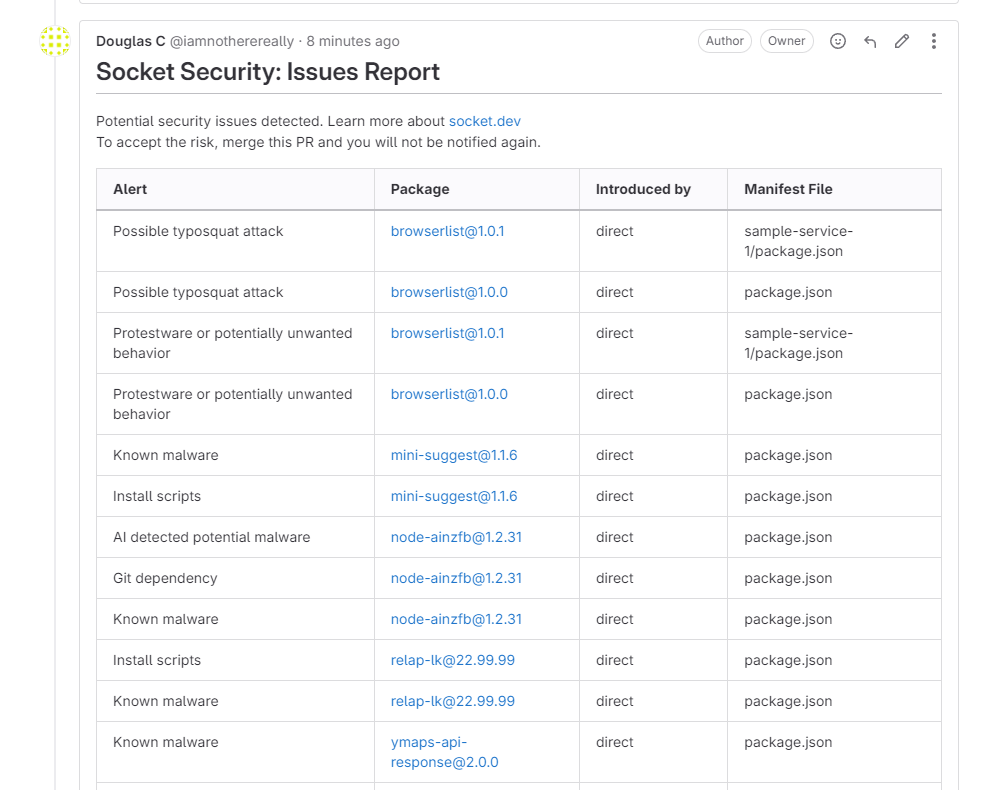
Updated about 1 month ago
That's it! You're all done now any time there is an update to your manifest file the Socket CI will automatically run. You can update the criteria to add more things like requirements.txt or other lock files.
