Sample Malware Packages
Sample Test Packages
Here are some example packages you can use to test out Socket alerts. All examples in this section are safe to install.
Typosquats
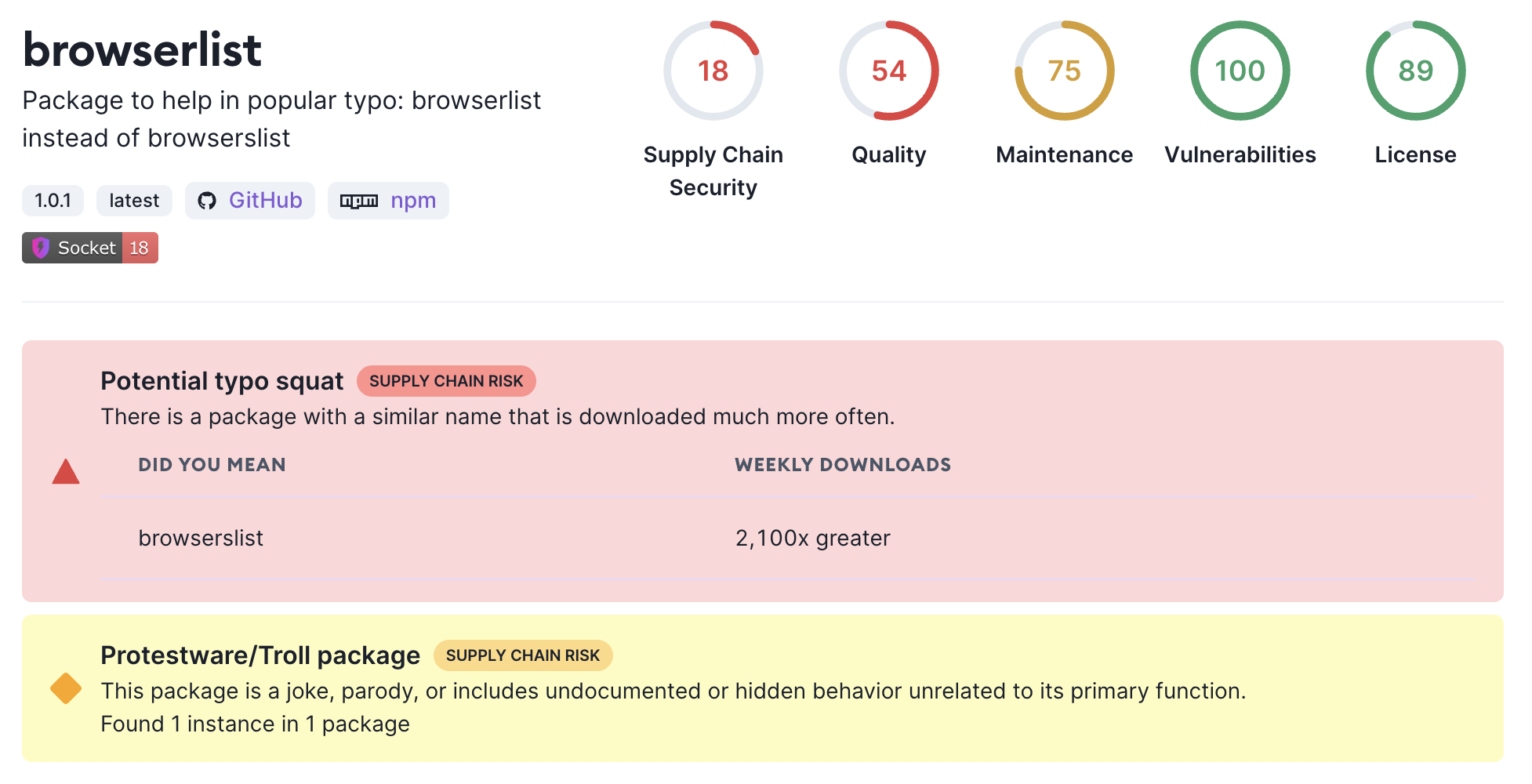
We recommend installing browserlist which is a typo of the much more popular package browserslist. When installing the typosquatted package, you should see an alert.
Telemetry
We recommend installing carbon-components which is a package that includes code that pings a server to track when the package is installed. While it may not be inherently malicious, it does pose a potential privacy risk as it collects and sends some system data back to IBM. Socket detects this package
Protestware/Troll package
We recommend installing [email protected] which contains unwanted hidden code. This package geolocates users based on their IP address and if the user is Russia-based prints a political protest message in the browser 15 seconds after the package is loaded. The package then tries to redirect the browser to another site using the window.open() function.
Recent Malware Examples (Detected By Socket)
If you want to see how Socket would perform on real malware npm packages, you can also look through our list of removed npm packages. Furthermore, here are several real examples:
Warning: The below packages are UNSAFE to installThey have already been removed from the package registry, but please exercise caution.
Malware executable
webb3– The code is likely malicious and should not be used.filebdecoder– This script is highly suspicious and potentially malicious. It downloads a Perl script from an external source and executes it on the system. This behavior can lead to unauthorized code execution and potential system compromise.node-click– The script downloads an executable from an external server and runs it on the user's system. This behavior can be malicious if the downloaded executable contains harmful code.
Obfuscated code
deahub(PyPI) – This file is encrypted with PyArmor.litter-woker– The script is obfuscated and dynamically creates functions to collect the user's environment variables and sends them to a remote server.pyautodllxd– The script is running a PowerShell command with a hidden window and an encoded command. This behavior is considered suspicious and could potentially execute malicious code on the system. The encoded command should be decoded and reviewed to determine the risk.koja_ali_jutt– This code is highly suspicious and should not be used without further investigation. The code is heavily obfuscated and could potentially contain malicious code. The purpose of the code is unclear and further investigation is necessary to determine its exact behavior.mrp-component-icon– This script contains obfuscated code, performs system checks, connects to an external server and directly executes the received response as JavaScript code. This represents a high security risk and possible malware, as the code it executes is dependent on the response from the external server. The server might serve malicious code. The usage of eval() function is also dangerous as it can lead to remote code execution vulnerabilities.
Reverse Shell
orange_papaya_greed– This script is highly suspicious and potentially malicious. It decodes a base64-encoded command and executes it using bash. This can allow arbitrary code execution on the system, which is a significant security risk.123rf-ui-core– The script creates a reverse shell, connecting the user's system to a remote IP address, and potentially sends data to an external server, posing a significant security risk.namatnawbyteweb1– This script is highly suspicious and indicates an attempt to establish a reverse shell connection to a remote server. This behavior is considered malicious and poses a significant security risk.vue3-babel-js– The code sets up a reverse shell using the 'tls' and 'child_process' modules, which can be used to gain unauthorized access to the user's systemnamatnawbyteweb6– This script is highly malicious and dangerous. It replaces the system shell and establishes a reverse shell connection, allowing unauthorized access to the system. It should be treated as malware and poses a significant security risk.
Data Exfiltration
airbnb-dls-web– This script is highly suspicious and potentially malicious. It attempts to exfiltrate system information and send it to a Telegram bot. It should be considered a significant security risk.js-integration-demo– This code is malicious and should not be used. Remove it from any system on which it is installed immediately. The remote server should be investigated to determine its legitimacy.segment-bundle– This code is using curl to send the contents of the file '/etc/passwd' to a remote server. This is a highly suspicious and potentially malicious behavior as it could cause sensitive data to be sent to an attacker's server.dvuln– This script fetches HTML from an external source, potentially allowing for injection of malicious content. It establishes a WebSocket connection to an external server, which could be used for exfiltrating data. The script sends user credentials and cookies to the external server, posing a threat to user privacy and security.
Socket In Action
You can see real-world examples of Socket scans detecting bad packages at our sample repo: SocketDemo/bitmidi.com.
Updated 5 months ago
