Socket for Bitbucket Pipeline
Socket fights vulnerabilities and provides visibility, defense-in-depth, and proactive supply chain protection for your open source dependencies. It is easy to integrate Socket into your Bitbucket Pipeline to provide an extra layer of security against Supply Chain Attacks.
Adding Socket to your pipeline
Create your Socket Environment variable
-
Create a Socket API Key (Directions)
-
Log into Bitbucket
-
Navigate to your repository
-
Go to Repository Settings
-
Go to Repository variables
-
Add a New variable
- Name: SOCKET_SECURITY_API_KEY
- Value: Your Socket API token
- Secured: Checked
-
Click Add
Example Bitbucket Pipeline Setup
-
Go to Source
-
Select the
...menu -
Select Add file
-
filename: bitbucket-pipelines.yml
-
Paste the following YAML or integrate into your existing pipeline
# Socket Security Bitbucket Pipelines # This pipeline runs Socket Security scans on every commit to any branch # The CLI automatically detects most information from the git repository image: socketdev/cli:latest definitions: steps: - step: &socket-scan name: Socket Security Scan script: # Run Socket CLI with minimal required parameters # The CLI automatically detects: # - Repository name from git # - Branch name from git # - Commit SHA from git # - Commit message from git # - Committer information from git # - Default branch status from git repository # - Changed files from git commit - | socketcli \ --scm bitbucket \ --pr-number ${BITBUCKET_PR_ID:-0} # Repository variables needed (set in Bitbucket repo settings) # SOCKET_SECURITY_API_KEY: Your Socket Security API token pipelines: # Run on all branches branches: '**': - step: *socket-scan # Run on pull requests pull-requests: '**': - step: *socket-scan
-
-
Commit changes to your main branch or the current branch you are working on
Testing pipeline
-
Create a new branch
-
Modify or add a
package.json -
Create a new Pull request
-
Confirm that the Socket CI pipeline job ran
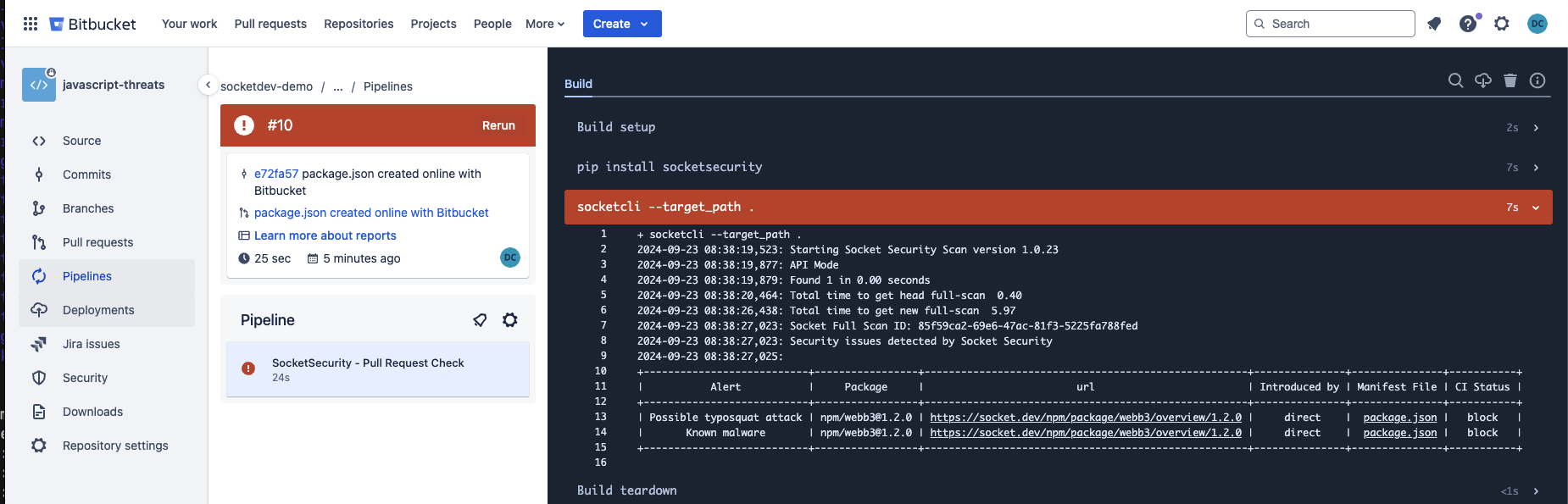
Updated 6 months ago
That's it! You're all done now any time there is an update to your manifest file the Socket CI will automatically run. You can update the criteria to add more things like requirements.txt or other lock files.
